DISCLAIMER: The content of this post/blog is based on opinion on what I have learned and for educational purposes, therefore if there are any mistakes or recommendation for improvement leave a comment 🙂
Brute Force is an attempt of attack on authentication by guessing a number of login credentials hoping that one of the credentials listed will work.
Common Tools for Brute Force:
- Burp Suite
- Hydra
- WPScan (Used Especially To Brute Force WordPress Admin)
In this post I will demonstrated how to brute force DVWA’s login even though the credentials are given in the DVWA github repository’s README.
For this post, I will use hydra to brute force DVWA‘s login.

We will require a wordlist for username and password to brute force the login.
Kali Linux already provide some word lists that penentration testers can use which has common login credentials.
Go to /usr/share/wordlists/metasploit and list directory. As you can see below there are alot of wordlists.
The ones we are going to use are:
- User Login: http_default_users.txt
- Password Login: http_default_pass.txt

NOTE: You can nano the word lists to check the words in the .txt file.
I used the following command to brute force with hydra:
#hydra -L http_default_users.txt -P http_default_pass.txt 127.0.0.1 http-form-post “/DVWA/login.php:username=^USER^&password=^PASS^&Login=Login:Login Failed”
The -L option specifies which word list file to use to brute force the username and -P option specifies which word list file to use to brute force the password.
Then after that specify IP of the Web Application with the type HTTP Request required after.
Then there are three arguments needed to be specified separated with a colon:
- The first argument is the URI to the login.
- The second argument is the parameter or data to be sent. Notice ^USER^ and ^PASS^ these are replace by username and password wordlist respectively.
- The third argument is the message to be printed if an attempt to Login failed.
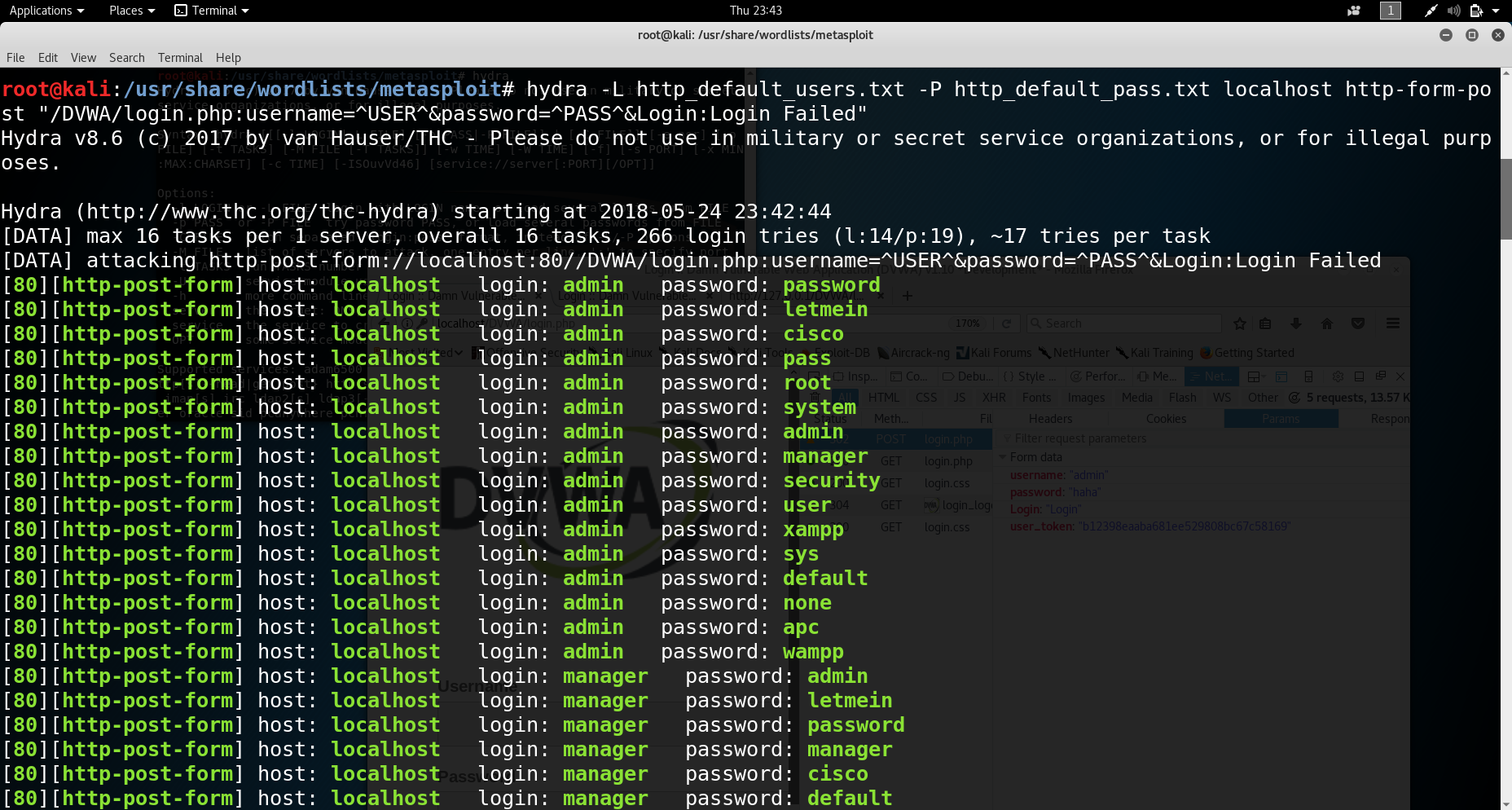
There is an issue, the issue is that there are many login credentials that are successful but in truth only one login credential is correct which is:
- Username: admin
- Password: password
The issue is that the Login uses a CSRF Token to protect it from Brute Force Attacks and submitting malicious requests.
CSRF (Cross Site Request Forgery) is mainly used to prevent users from executing actions that they do not want to when they are authenticated.
The picture below shows the token provided in the Form.

Conclusion, I have not found a way to successfully brute force DVWA login but hopefully in a later post, I can successfully brute force it.
Result after Login:
Thank you 🙂
